Experts from Heimdal Security warned of a spike in cyber attacks leveraging the popular RIG Exploit kit to deliver the Cerber Ransomware.
The RIG exploit kit is even more popular in the criminal ecosystem, a few days ago security experts at Heimdal Security warned of a spike in cyber attacks leveraging the popular Neutrino and RIG EKs.
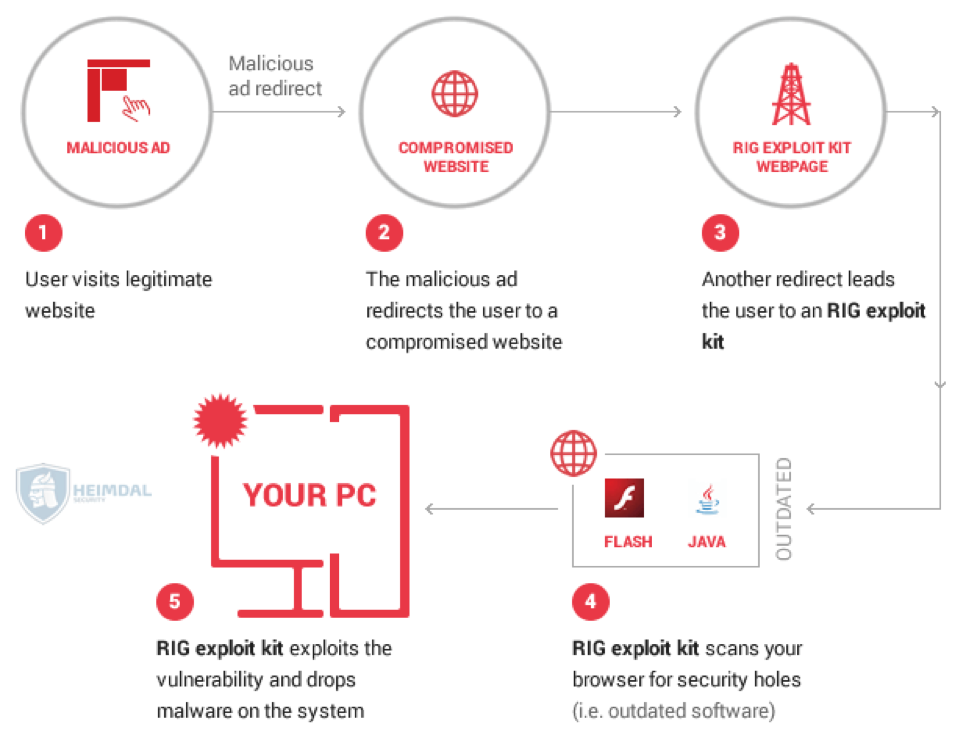
Now security experts from Heimdal Security are warning of a new campaign leveraging the RIG exploit kit that targets outdated versions of popular applications to distribute the Cerber ransomware.
The attackers leverage an array of malicious domains to launch drive-by attacks against visitors trying to exploit flaws in outdated versions of popular applications such as Flash, Internet Explorer, or Microsoft Edge.
“At the moment, cybercriminals are using a swarm of malicious domains to launch drive-by attacks against unsuspecting users.” states the analysis published by Heimdal Security.
“The campaign works by injecting malicious scripts into insecure or compromised systems. Victims can get infected simply by browsing the compromised or infected websites, without clicking on anything. What exposes them to this attack are outdated versions of the following apps: Flash Player, Silverlight, Internet Explorer or Edge.”
The crooks compromise websites to inject malicious scripts that allow exploiting the flaws in the victim’s browser even without user interaction. reports.

This new campaign leverages on a RIG exploit kit that attempts to exploit the following 8 vulnerabilities:
- CVE-2015-8651
- CVE-2015-5122
- CVE-2016-4117
- CVE-2016-1019
- CVE-2016-7200
- CVE-2016-7201
- CVE-2016-3298
- CVE-2016-0034
According to the experts from Heimdal security, this variant of the RIG exploit is the Empire Pack version (RIG-E). Cyber criminals also abused domains that are part of the so-called Pseudo-Darkleech gateway that was also exploited by cyber gangs in June 2016 to deliver the CryptXXX ransomware in several campaigns leveraging on the Neutrino Exploit Kit.
It is important to highlight that the success of campaigns like this one is determined by the failure in applying security updates in popular software.
“As you can see, cybercriminals often use vulnerabilities already patched by the software developer in their attacks, because they know that most users fail to apply updates when they’re released. In spite of the wave of attacks, many Internet users still choose to ignore updates, but we hope that alerts such as this one will change their mind and make them more aware of the key security layer that updates represent.” states the report.
[adrotate banner=”22″]